Used to generate bulk pull requests (PRs) against projects to fix security vulnerabilities.
These 'bulk fixes' are done as a part of the new GitHub Security Lab Bug Bounty Program.
Data is sourced from queries on lgtm.com and used to create bulk pull-requests to fix these security vulnerabilities.
- Built-in crash recovery -- Saves state during execution to allow recovering from a crash
- Records metrics -- Files fixed, Number of Fixes, PR URLs
- Fast -- Asynchronous IO using python async API
- Commit messages follow the SECOM standard.
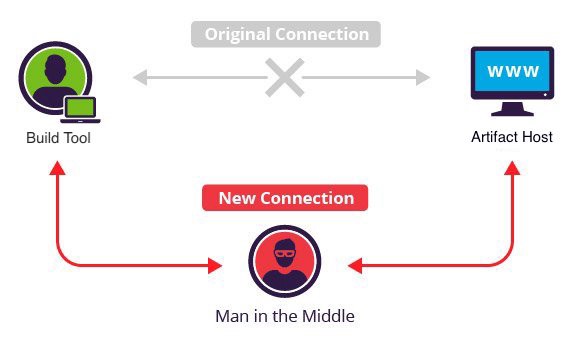
Want to take over the Java ecosystem? All you need is a MITM!
This project has been used to generate PRs that automatically fix a security vulnerability in Maven POM files that are using HTTP instead of HTTPS to resolve dependencies.
Pull Requests Generated: 1,596
GitHub Security Lab's pwntester leveraged this project to generate pull requests to fix an array overflow. This is a variant of CVE-2020-8597.
You can read in more detail about this vulnerability in CERT Advisory VU#782301.
The vulnerability occurs because, given that vallen was checked to be less than len, it can never be the case that vallen >= len + sizeof(rhostname). Therefore, rhostname never gets trimmed and the rhostname array may overflow.
Pull Requests Generated: 1,885
In 2019, I discovered a vulnerability in the JHipster code generator where it was
generating vulnerable implementations of a class called RandomUtil.java.
Using one password reset token from these apps combined with the POC below, an attacker can determine all future password reset tokens to be generated by these vulnerable servers. This would allow an attacker to pick and choose what account they would like to takeover by sending account password reset requests for targeted accounts.
POC code has existed since March 3rd, 2018 for taking one RNG value generated by RandomStringUtils and reversing it to generate all of the past/future RNG values.
The fix was generated for each vulnerable file, preserving the original style of the file, by the Rewrite project. See the specific code for this fix here.
Pull Requests Generated: 3,880