A tool that can combine fofa and xray for automatic batch multithreading scanning.
Can also scan the IP/domain name list by using Xray.
Coding by golang, both for windows, linux and macOS.
Use fofa api to get target domain list, then make webscan by xray.
./fofa2Xray -t file -f ipList.txt-
-
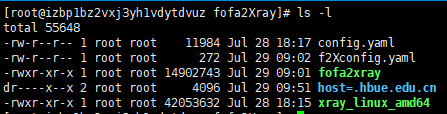
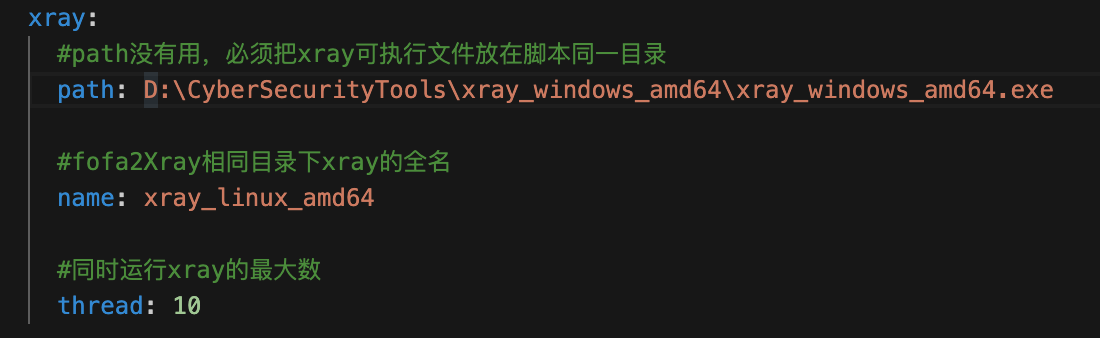
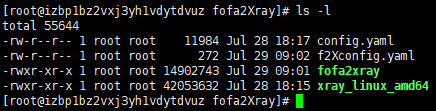
fofa: email: {fofa账户} key: {fofaKey} # 固定查询语句 fixedQuerySyntexList: - status_code=200 - country="CN" # 查询语法 # 更多查询语法见https://fofa.info/ querySyntax: host # 使用querySyntax查询语法分别查询target targetList: - .hubu.edu.cn # - .hbue.edu.cn # - .wust.edu.cn xray: #path没有用,必须把xray可执行文件放在脚本同一目录 path: D:\CyberSecurityTools\xray_windows_amd64\xray_windows_amd64.exe #fofa2Xray相同目录下xray的全名 name: xray_windows_amd64.exe #同时运行xray的最大数 thread: 10
-
./fofa2Xray nohup ./fofa2Xray & // 持久化
-
Fofa2Xray will create result folder for every target.